Sunday
HOW TO GET ANY WINDOWS PASSWORD
Saturday
Find Any Serial 100%

How to fix corrupted files in XP
Securing WinXP Pro (with what win-xp has to offer)
after my default install. These changes will not secure your box 100% but they
make a good couple of 1st steps. They are in no specific order other than the
order that I performed them. I have only spent a couple of hours working on
this operating system at the time of this text so please bare with me and
understand that there is much more to securing your box than this.
1. NTFS Partition.
2. Disable Error Reporting
3. Disable Automatic Updates (only if your XP copy is pirated)
4. Disable "Recent Documents" Viewed
5. Setup XP Firewall
6. Setup screensaver password
7. Setup BIOS password
8. Setup "AfterBios" login password
9. Account Modifications
-Rename Admin Account
-Disable Guest Account
-Disable Help_Assistant Account
-Disable Support Account
10. Install a virus scanner.
11. Change Login Screen (default shows usernames)
12. Disable Remote Registry (and other services)
13. Disable/Change Auto-Search settings in IE.
1. -----------------------------------------------------------------------------------------
NTFS Partition (I like being God over system users)
-----------------------------------------------------------------------------------------
Be sure to install XP onto an NTFS partition so that you (the admin) can take advantage
of file permissions. You want this option so that "you" can decide who reads, writes,
executes what files.
If you didnt install XP onto an NTFS partition. Convert It. To convert to NTFS follow
the instructions below.
Open a command prompt and type "convert c: /FT:NTFS /v"
This command will convert your c: partition from FAT to NTFS in verbose mode.
2. -----------------------------------------------------------------------------------------
Disable Error Reporting - we dont want microsoft to know everytime we fuck up.
especially if we didnt pay for winxp.
-----------------------------------------------------------------------------------------
control panel >> performance and maintenance >> system >> advanced >> error reporting
(disable all)
right click "my computer" >> manage >> services and applications >> services >> " stop
and disable" Error Reporting.
3. -----------------------------------------------------------------------------------------
Disable automatic updates - to update, they must know what we have. thats a NO NO!
-----------------------------------------------------------------------------------------
NOTE: DO THIS ONLY IF YOUR COPY OF XP IS PIRATED!! I suggest "auto update" if your copy
of XP is legal. If your copy is pirated then i suggest that you stay updated with
the latest fixes and patches manually.
control panel >> performance and maintenance >> system >> automatic updates
(disable updates)
right click "my computer" >> manage >> services and applications >> services >> " stop
and disable" Automatic Updates.
4. -----------------------------------------------------------------------------------------
Quit listing most recent documents opened under the start button - Dont want the
girlfriend or the parents to find that pr0n you being viewing.
-----------------------------------------------------------------------------------------
control panel >> appearance and themes >> task bar and start menu >> start menu >>
customize >> advanced
remove the checkmark next to "List my most recently opened documents".
5. -----------------------------------------------------------------------------------------
Block incoming traffic to your winxp box. - Before this change, i scanned my xp box and
found it to have many ports wide open. After this change, I found nothing and xp logged
the attempts in c:\windows\pfirewall.log.
-----------------------------------------------------------------------------------------
control panel >> network connections >> right click "local area connection" >> properties
>> advanced >> check the box under "Internet Connection Firewall" then choose "settings".
Services Tab - leave all unchecked unless there is a service you are running that people
must be able to access.
Logging Options - Log everything.
ICMP - I left all these unchecked for the time being. (allowing nothing)
(this does not protect you from "Spy Ware". This only stops traffic from coming into
your win-xp box (not all traffic). It does not stop traffic from going out.) If you
need to stop traffic from going out and need a more secure firewall then download a real
firewall like "zone alarm or black ice".
6. -----------------------------------------------------------------------------------------
Setting a screensaver password incase you leave some of that secret pr0n open when you
walk away.
-----------------------------------------------------------------------------------------
right click on the desktop >> properties >> screen saver >> check the box next to " On
Resume, Password Protect."
If you dont have a password set on your user account, you can do so in control panel >>
user accounts >> change account.
7. -----------------------------------------------------------------------------------------
Setting a BIOS password - We dont want anyone rebooting the computer or trying to sneak
into our pr0n while we are away at school or work.
-----------------------------------------------------------------------------------------
I cant explain to one how this is done due to the differences between all computers and
how the BIOS settings are entered. If you know what Im talking about then do it. If you
dont know what Im talking bout then learn how to do it. A screensaver password is useless
unless you setup a BIOS password.
8. ------------------------------------------------------------------------------------------
Setting up the "AfterBios" password. Sometimes bios passwords are easily cracked. This
password will add extra local login security incase your bios pass is crax0red. I dont
know bout you but i love having to type in 3 passwds and a username to login to my box.
------------------------------------------------------------------------------------------
Start >> run >> type "syskey" >> choose "update" >> choose "Password Startup" >> enter a
password and choose ok.
9. ------------------------------------------------------------------------------------------
Renaming and Disabling Accounts for adminstrator, guest, help_assistant and support.
------------------------------------------------------------------------------------------
Right click my_computer >> manage >> local users and groups
rename administrator account
disable guest account
disable help_assistant account
disable support account
10. -------------------------------------------------------------------------------------------
Install Virus Protection............. (We like our uncorrupted data and trojan free system)
-------------------------------------------------------------------------------------------
Install a virus scanner. Your firewall might protect your system from unwanted hackers but
what about an unwanted virus or trojan?. I recommend installing a virus scanner such as
"Nortons" or "McAfee".
11. -------------------------------------------------------------------------------------------
Change Default Login Screen............ (why do we want to share usernames with anyone?)
-------------------------------------------------------------------------------------------
Xp uses the "welcome screen" by default. This screen has the names of all accounts on the
system so that the user only has to click on their name and type a password. Come on now....
We arent that damn lazy. If we change this screen to the normal login, then prying eyes
will have to know a username and password to get in. Follow the instruction below to change
this.
control panel >> user accounts >> change the way users log on or off
uncheck the box next to "Use Welcome Screen" and choose "apply options".
12. -------------------------------------------------------------------------------------------
Disable Remote Registry..........(why would I need to edit my registry remotely anyway?)
-------------------------------------------------------------------------------------------
right click "my computer" >> manage >> services and applications >> services >> " stop
and disable" Remote Registry.
NOTE: disable any services running in this area that you arent using.
13. -------------------------------------------------------------------------------------------
Disable/Change Auto-search in Internet Explorer. This is not really a security risk but it
is important to some people that prefer to keep their internet surfing to themselves and
away from microsoft.
-------------------------------------------------------------------------------------------
Open Internet Explorer >> Click the "search" button >> click the "customize" button >> click
"autosearch settings" >> FOLLOW INSTRUCTIONS BELOW...........
DISABLE: In the "When Searching" drop down menu, select "Do not search from the address bar".
>> click "ok" >> "ok". Type an invalid address in your address bar and see if it
takes you to the msn search page or if it gives a "page not found" error. In this
case, the "page not found" error is what we want.
CHANGE: If you wish not to disable, but you wish to change it to your favorite "google.com"
search page. Instead of following the "DISABLE" instructions, follow the instructions
below. Choose "Google Sites (or whatever you prefer)" from the "choose a search provider
to search from address bar" drop down menu >> click "ok" >> "ok"
SINGLE CLICK SHUTDOWN
All you need to do is... right-click on an empty Desktop spot -> select New -> Shortcut -> type shutdown followed by a space, and then enter one or more of the parameters listed below -> click Next -> type a suggestive name for your new shortcut -> finally, click Finish.
This is the Shutdown.exe (located in %systemroot%\System32, usually C:\Windows\System32) syntax:
shutdown [-i|-l|-s|-r|-a] [-f] [-m \\computername] [-t xx] [-c "Text"] [-d[u][p]:xx:yy]
Valid command line switches:
-a = Abort system shutdown in progress ONLY IF the -t xx timeout option was already set to ANY value other than 0. ALL switches except -l and -m are ignored during abort.
-c "Text" = Text comment (case insensitive) to be displayed in the Message area of the System Shutdown window. MUST be enclosed between quotes. Maximum allowed 127 ASCII characters.
-d [u][p]:xx:yy = Reason code for shutdown:
u = User code.
p = Planned shutdown code.
xx = Major reason code. Positive integer number less than 256.
yy = Minor reason code. Positive integer number less than 65536.
-f = Force running applications to close without warning.
-i = Display the shutdown interface (GUI). MUST be the first option!
-l = Log off the current user of the local computer (default action). Can NOT be used with the -m option unless the current user has Sysadmin rights, in which case the -m switch takes precedence.
-m \\computername = Remote/network computer name (most always case sensitive) to log off/restart/shut down. Current user MUST have Sysadmin rights to be allowed to use this switch!
-s = Shut down the local computer.
-r = Shut down and restart (reboot) the local computer.
-t xx = Set shutdown timer to timeout for xx seconds. IF NOT specified defaults to 20 seconds. Allowed values between 0 and 99 seconds. The -a switch is the ONLY one that CAN be used during the timeout period.
NOTES:
The dash (-) in front of these switches can be replaced by a forward slash (/).
Spaces are NOT required to separate the shutdown command from ANY following switches, but ARE required to separate ANY switch from its following parameter(s), if any.
For example:
shutdown -s -c "Shutting down!" -t 3
tells your computer to shutdown after waiting for 3 seconds while the System Shutdown window will display text above in the Message area.
Optional: after you're done creating your customized shortcut for shutdown -> right-click on it -> select Properties -> enter your desired key "combo" in the Shortcut Key box (e.g. Ctrl + Alt + End) -> click OK/Apply.
From now on just left-click on your shutdown shortcut or hit that key combination to turn off/restart/log off your computer.
100 ebook Finding with Google
Here are some tips to helps you find eBooks with Google:
Find Apache's (default) Index page
Try this query:
+("index of") +("/ebooks"|"/book") +(chm|pdf|zip|rar) +apache
Find a particular eBook file
Try this query:
allinurl: +(rar|chm|zip|pdf|tgz) TheTitle
Browser Hijacking
In addition to having third party utilities such as SpyBot, Anti Virus scanners and firewalls installed there are some changes that can be made to Windows 2000/XP. Below are some details to make your system safer from hackers and hijackers.
Some of these tips require editing of the Registry so it is wise to either backup the registry and/or create a Restore Point.
1. Clearing the Page File at Shutdown
Windows 2000/XP paging file (Sometimes called the Swap File) can contain sensitive information such as plaintext passwords. Someone capable of accessing your system could scan that file and find its information. You can force windows to clear out this file.
In the registry navigate to HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSession ManagerMemory Management and add or edit the DWORD ClearPageFileAtShutdown. Set it to 1.
Note that when you do this, the system will take much longer to shut down: a system with a really big Page File (! Gig or more) may take a minute or two longer.
2. Disable the POSIX and OS/2 Subsystem.
Windows 2000 and XP come with little-documented subsystems it at allow compatibility with UNIX and OS/2 systems These rues systems are enabled by default but so rarely used that they are best off bring disabled completely to prevent possible service hijackings.
To disable these subsystems, open the registry and navigate to HKEY LOCAL MACHINESYSTEMCurrentControlSetControlSession ManagerSubSystems. Delete the subkeys Os2 and Posix. then reboot.
On installation, Windows 2000 sets up an Administrator account with total system access and prompts for a password. Guess what: by default, it allows that password to be blank. If a user doesn't want to type a password, he can simply click Next and the system will be an open door for anyone who wants to log on. Always opt for a password of some kind when setting up the default account on a machine.
Windows usually installs itself in the WINDOWS directory. Windows NT 4 0 and 2000 Will opt for WINNT. Many worms and other rogue programs assume this to be the case and attempt to exploit those folders files. To defeat this install Windows to another directory when you're setting it up - you can specify the name of the directory during setup. WINDIR is okay; so some people use WNDWS - A few (not that many) programs may not install properly if you install Windows to another folder but t hey are very few and they are far between
Since the default account in Windows 2000 is always named Administrator, an enterprising hacker can try to break into your system by attempting to guess the password on that account. It you never bothered to put a password on that account, say your prayers.
Rather than be a sucker to a hacker, put a password on the Administrator account it you haven't done so already. Then change the name of the Administrator account. You'll still be able to use the account under its new name, since Windows identifies user accounts by a back-end ID number rather than the name. Finally, create a new account named Administrator and disable it. This should frustrate any would -be break-ins.
You can add new accounts and change the names of existing accounts in Windows 2000 through the Local Users and Groups snap in. Right-click on My Computer, select Manager, open the Local Users and Groups subtree, look in the Users folder and right-click on any name to rename it. To add a new user, right-click on the containing folder and select New User. Finally, to disable an account, double-click it, check the Account is disabled box and click OK.
Don't ever delete the original Administrator account. Some programs refuse to install without it and you might have to log in under that account at some point to setup such software. The original Administrator account is configured with a security ID that must continue to be present in the system.
Windows XP comes with a Guest account that's used for limited access, but it's still possible to do some damage with it. Disable it completely if you are not using it. Under Control Panel, select User Accounts, click on Guest Account and then select Turn Off the Guest Account.
This one's from (and to a degree, for) the experts. The HOSTS file is a text file that all flavors of Windows use to hold certain network addresses that never change. When a network name and address is placed in HOSTS, the computer uses the address listed there for that network name rather than performing a lookup (which can take time). Experts edit this file to place their most commonly-visited sites into it, speeding things up considerably.
Unfortunately hijackers and hackers also love to put their own information into it - redirecting people from their favorite sites to places they don't want to go. One of the most common entries in HOSTS is local host which is set 1770.0.1. This refers to the local machine and if this entry is damaged the computer can behave very unpredictably.
To prevent HOSTS from being hijacked, set it to read-only. Go to the folder %Systemroot%system32driversetc, right-click on HOSTS, select Properties check the Read-Only box and click OK. If you want to add your own entries to HOSTS, you can unprotect it before doing so, but always remember to set it to read-only after you're done.
This is another anti hijacker tip. IE can be set so that any changes to its settings must be performed through the Internet icon in the Control Panel, rather than through IE's own interface. Some particularly unscrupulous programs or sites try to tamper with setting by accessing the Tools, Options menu in IE. You can disable this and still make changes to IE's settings through the Control Panel.
Open the Registry and browse to HKEY_CURRENT_USER SoftwarePoliciesMicrosoftInternet ExplorerRestrictions. Create or edit a new DWORD value named NoBrowserUptions and set it to 1 (this is a per-user setting). Some third-party programs such as Spybot Search And Destroy allow you to toggle this setting.
You can also keep IE from having other programs rename its default startup page, another particularly annoying form of hijacking. Browse to HKEY.CURRENT USERSoftwarePolicies MicrosoftInternet ExploreControl Panel and add or edit a DWORD, Homepage and set it to 1.
Windows 2000 and XP both come with many background services that don't need to he running most of the time: Alerter, Messenger, Server (If you're running a standalone machine with no file or printer shares), NetMeeting Remote Desktop Sharing, Remote Desktop Help Session Manager (the last two if you're not using Remote Desktop or NetMeeting), Remote Registry, Routing and Remote Access (if you're not using Remote Access), SSDP Discovery Service, Telnet, and Universal Plug and Play Device Host.
A good resource and instruction on which of these services can be disabled go to /http://www.blkviper.com/WinXP/
In Windows XP Professional, the Simple File Sharing mode is easily exploited, since it’s a little too easy to share out a file across your LAN (or the NET at large). To turn it off, go m My Computer, click Tools, Folder Option and the View tab, and uncheck Use Simple file sharing (Recommended). Click OK. When you do this you can access the Security tab in the Properties window for all folders; set permissions for folders; and take ownership of objects (but not in XP Home)
How to Bypass BIOS Passwords

This article is intended for IT Professionals and systems administrators with experience servicing computer hardware. It is not intended for home users, hackers, or computer thieves attempting to crack the password on a stolen PC. Please do not attempt any of these procedures if you are unfamiliar with computer hardware, and please use this information responsibly. LabMice.net is not responsible for the use or misuse of this material, including loss of data, damage to hardware, or personal injury.
Before attempting to bypass the BIOS password on a computer, please take a minute to contact the hardware manufacturer support staff directly and ask for their recommended methods of bypassing the BIOS security. In the event the manufacturer cannot (or will not) help you, there are a number of methods that can be used to bypass or reset the BIOS password yourself. They include:
Using a manufacturers backdoor password to access the BIOS
Use password cracking software
Reset the CMOS using the jumpers or solder beads.
Removing the CMOS battery for at least 10 minutes
Overloading the keyboard buffer
Using a professional service
Please remember that most BIOS passwords do not protect the hard drive, so if you need to recover the data, simply remove the hard drive and install it in an identical system, or configure it as a slave drive in an existing system. The exception to this are laptops, especially IBM Thinkpads, which silently lock the hard drive if the supervisor password is enabled. If the supervisor password is reset without resetting the and hard drive as well, you will be unable to access the data on the drive.
---------------------------------------------------------------------------
Backdoor passwords
Many BIOS manufacturers have provided backdoor passwords that can be used to access the BIOS setup in the event you have lost your password. These passwords are case sensitive, so you may wish to try a variety of combinations. Keep in mind that the key associated to "_" in the US keyboard corresponds to "?" in some European keyboards. Laptops typically have better BIOS security than desktop systems, and we are not aware of any backdoor passwords that will work with name brand laptops.
WARNING: Some BIOS configurations will lock you out of the system completely if you type in an incorrect password more than 3 times. Read your manufacturers documentation for the BIOS setting before you begin typing in passwords
Award BIOS backdoor passwords:
ALFAROME ALLy aLLy aLLY ALLY aPAf _award AWARD_SW AWARD?SW AWARD SW AWARD PW AWKWARD awkward BIOSTAR CONCAT CONDO Condo d8on djonet HLT J64 J256 J262 j332 j322 KDD Lkwpeter LKWPETER PINT pint SER SKY_FOX SYXZ syxz shift + syxz TTPTHA ZAAADA ZBAAACA ZJAAADC 01322222
589589 589721 595595 598598
AMI BIOS backdoor passwords:
AMI AAAMMMIII BIOS PASSWORD HEWITT RAND AMI?SW AMI_SW LKWPETER A.M.I. CONDO
PHOENIX BIOS backdoor passwords:
phoenix, PHOENIX, CMOS, BIOS
MISC. COMMON PASSWORDS
ALFAROME BIOSTAR biostar biosstar CMOS cmos LKWPETER lkwpeter setup SETUP Syxz Wodj
OTHER BIOS PASSWORDS BY MANUFACTURER
Manufacturer Password
VOBIS & IBM merlin
Dell Dell
Biostar Biostar
Compaq Compaq
Enox xo11nE
Epox central
Freetech Posterie
IWill iwill
Jetway spooml
Packard Bell bell9
QDI QDI
Siemens SKY_FOX
TMC BIGO
Toshiba Toshiba
TOSHIBA BIOS
Most Toshiba laptops and some desktop systems will bypass the BIOS password if the left shift key is held down during boot
IBM APTIVA BIOS
Press both mouse buttons repeatedly during the boot
---------------------------------------------------------------------------
Password cracking software
The following software can be used to either crack or reset the BIOS on many chipsets. If your PC is locked with a BIOS administrator password that will not allow access to the floppy drive, these utilities may not work. Also, since these utilities do not come from the manufacturer, use them cautiously and at your own risk.
Cmos password recovery tools 3.1
!BIOS (get the how-to article)
RemPass
KILLCMOS
---------------------------------------------------------------------------
Using the Motherboard "Clear CMOS" Jumper or Dipswitch settings
Many motherboards feature a set of jumpers or dipswitches that will clear the CMOS and wipe all of the custom settings including BIOS passwords. The locations of these jumpers / dipswitches will vary depending on the motherboard manufacturer and ideally you should always refer to the motherboard or computer manufacturers documentation. If the documentation is unavailable, the jumpers/dipswitches can sometimes be found along the edge of the motherboard, next to the CMOS battery, or near the processor. Some manufacturers may label the jumper / dipswitch CLEAR - CLEAR CMOS - CLR - CLRPWD - PASSWD - PASSWORD - PWD. On laptop computers, the dipswitches are usually found under the keyboard or within a compartment at the bottom of the laptop.
Please remember to unplug your PC and use a grounding strip before reaching into your PC and touching the motherboard. Once you locate and rest the jumper switches, turn the computer on and check if the password has been cleared. If it has, turn the computer off and return the jumpers or dipswitches to its original position.
---------------------------------------------------------------------------
Removing the CMOS Battery
The CMOS settings on most systems are buffered by a small battery that is attached to the motherboard. (It looks like a small watch battery). If you unplug the PC and remove the battery for 10-15 minutes, the CMOS may reset itself and the password should be blank. (Along with any other machine specific settings, so be sure you are familiar with manually reconfiguring the BIOS settings before you do this.) Some manufacturers backup the power to the CMOS chipset by using a capacitor, so if your first attempt fails, leave the battery out (with the system unplugged) for at least 24 hours. Some batteries are actually soldered onto the motherboard making this task more difficult. Unsoldering the battery incorrectly may damage your motherboard and other components, so please don't attempt this if you are inexperienced. Another option may be to remove the CMOS chip from the motherboard for a period of time.
Note: Removing the battery to reset the CMOS will not work for all PC's, and almost all of the newer laptops store their BIOS passwords in a manner which does not require continuous power, so removing the CMOS battery may not work at all. IBM Thinkpad laptops lock the hard drive as well as the BIOS when the supervisor password is set. If you reset the BIOS password, but cannot reset the hard drive password, you may not be able to access the drive and it will remain locked, even if you place it in a new laptop. IBM Thinkpads have special jumper switches on the motherboard, and these should be used to reset the system.
---------------------------------------------------------------------------
Overloading the KeyBoard Buffer
On some older computer systems, you can force the CMOS to enter its setup screen on boot by overloading the keyboard buffer. This can be done by booting with the keyboard or mouse unattached to the systems, or on some systems by hitting the ESC key over 100 times in rapid succession.
---------------------------------------------------------------------------
Jumping the Solder Beads on the CMOS
It is also possible to reset the CMOS by connecting or "jumping" specific solder beads on the chipset. There are too many chipsets to do a breakdown of which points to jump on individual chipsets, and the location of these solder beads can vary by manufacturer, so please check your computer and motherboard documentation for details. This technique is not recommended for the inexperienced and should be only be used as a "last ditch" effort.
---------------------------------------------------------------------------
Using a professional service
If the manufacturer of the laptop or desktop PC can't or won't reset the BIOS password, you still have the option of using a professional service. Password Crackers, Inc., offers a variety of services for desktop and laptop computers for between $100 and $400. For most of these services, you'll need to provide some type of legitimate proof of ownership. This may be difficult if you've acquired the computer second hand or from an online auction.
Hacking.exe File
Couse that's for programmers and assembly experts only. If any of you dumb kids
try to view it in hex you'll only get tons of crap you don't understand.
First off, you need Resource Hacker(last version).It's a resource editor-
very easy to use.
Resource Hacker Version 3.4.0
CODE
http://delphi.icm.edu.pl/ftp/tools/ResHack.zip/
Help File
CODE
http://www.users.on.net/johnson/resourceha...eshack_hlp.zip/
################################################################################
2)Unzip the archive, and run ResHacker.exe. You can check out the help file too,
if you want to be a guru.
################################################################################
3)You will see that the interface is simple and clean. Go to the menu File\Open or
press Ctrl+O to open a file. Browse your way to the file you would like to edit.
You can edit *.exe, *.dll, *.ocx, *.scr and *.cpl files, but this tutorial is ment
to teach you how to edit *.exe files, so open one.
################################################################################
#
4)In the left side of the screen a list of sections will appear.
The most common sections are: -Icon;
-String table;
-RCData;
-Dialog;
-Cursor group;
-Bitmap;
-WAV.
*Icon: You can wiew and change the icon(s) of the program by double-clicking the icon section,chossing the icon, right-clicking on it an pressing "replace resource". After that you can choose the icon you want to replace the original with.
*String table: a bunch of crap, useful sometimes, basic programming knowladge needed.
*RCData: Here the real hacking begins. Modify window titles, buttons, text, and lots more!
*Dialog:Here you can modify the messages or dialogs that appear in a program. Don't forget
to press "Compile" when you're done!
*Cursor group: Change the mouse cursors used in the program just like you would change the icon.
*Bitmap: View or change images in the programs easy!
*WAV:Change the sounds in the prog. with your own.
################################################################################
####
5) In the RCData,Dialog,Menu and String table sections you can do a lot of changes. You can
modify or translate the text change links, change buttons, etc.
################################################################################
TIP: To change a window title, search for something like: CAPTION "edit this".
TIP: After all operations press the "Compile Script" button, and when you're done editing save
your work @ File\Save(Save as).
TIP: When you save a file,the original file will be backed up by default and renamed to Name_original and the saved
file will have the normal name of the changed prog.
TIP: Sometimes you may get a message like: "This program has a non-standard resource layout... it has probably been compressed with an .EXE compressor." That means that Resource Hacker can't modify it becouse of it's structure.
Remember! This is only a small example of what you can do to executables with Resource Hacker.
PS2 Without ModChip
You will need the following things to burn PS2 games:
a computer with a cd burner
a blank cd-r (don't use the re-recordable type a.k.a. cd-rw)
CDRWIN – The version in this guide is 3.8D
FireBurner –
PS2 patcher –
GameShark 2 for PS2 - the GameShark 2 is available at most stores that sell video games, a few examples would be Best Buy, Circuit City, or Target. You want version 1.0 of the GameShark 2. I have heard that all other versions work, but I have only tested version 1.0. GameShark2 costs about 29.95. Believe me, its worth it!!!
and a PS2 to play the games.
Burning the PS2
The process of burning ps2 games is easy. It is really only a 3 step process.(read the game, patch the game, and burn the game.)
1) insert game into cd drive.
2) Open up CDRWIN and click on the extract disk/tracks/sectors button.
3) Your settings should be as follows:
For "extract mode” select disk image/ cue sheet
For "read options” select "raw”
For "error recovery” select "abort”
For "jitter correction” select "auto”
For "subcode analysis” select "auto”
Data Speed and Audio Speed should be the same
For "read retry count” type 0
For "subcode threshold” type 300
Make sure you selected the drive that your PS2 game is in
Make sure you typed in the file name (just type the name of the game) and Check the directory that you're putting your file in.
Then just press "start”
If you get an error in the middle of reading the disk that says something like "can't read sections xxxx-xxxxx of disk”, it is becase the disk is scratched and CDRWIN can't read it. Try to clean the disk, if that doesn't work you just have to use a different game (a different copy of the same game)
4) Once CDRWIN is done, click ok and then exit CDRWIN. Open up the PS2 patcher, select the game file you just created and patch it (make sure you select the "RAW” option.
5) Close the PS2 patcher, next open up Fireburner. Click on the visual cue burner button. When you created your .bin file (the game file) in CDRWIN, a .cue file should have automaticly been created. In that case, drag and drop the .cue file into the Fireburner window. If the .cue file was not created, just drag and drop the .bin file into the Fireburner window. After you have done that, right click (click with the right side button on your mouse) on your file in the Fireburner window, and select "Burn/Test burn”.
6) In the options window that appears, select your cdwriter, select your write speed(doesn't really matter), and make sure you select "Track at once (TOA) for the recording method. As for the options on the right side of the options window, make sure only the following are checked: "eject cd” and "close session”.
When you have selected the options, click ok and your PS2 game will burn. That's all you have to do to burn a game.
Burning a Playstion (PSone) game
1) If you want, you can spend 5 minutes using the same method as above to burn your playstation game, but its not necessary. For a playstation game (not PS2) all you need to do is use a program that lets you make an "exact copy” or a "backup disk (CDRWIN)” You don't need any selected options, you just need to start the game on the PS2 the same way you would a PS2 game.
Starting the game on your PS2
1) Now for the fun part (and challenging part the first couple of times) This may sound a little complicated at first, but after you do it 3 or 4 times, it's super easy. First things first, you must remove the front of your game drive on your PS2(not a big deal, it can snap on and off).
2) Now insert your gameshark 2 cd(make sure the gameshark memory card is in one of the 2 slots, doesn't matter which one.)
3) In the gameshark options, choose "start game”, then "without”. Your screen should read "Please insert game disk then press X to continue.”
4) Now this part can be trickey for beginners, so I will provide pictures
-the main purpose of this starting method is to open up the PS2 and swap the gameshark disk with your burned game without the PS2 knowing you did it. DO NOT press the eject button on the PS2!!!
-with the PS2 cd tray cover removed, you will be able to look in and see a while tab inside the PS2. With a credit card (or something like it) gently slide the white tab all the way over to the right, if you did it correctly, this should allow you to manually pull open the PS2 cd tray.
5) Next, take the gameshark disk out of the PS2 and put in your burned game.
6) Gently push the PS2 cd tray fully back into the PS2 (Don't press the eject button).
7) Now you need to slide that white tab all the way back to the left (its origional position). To do this you get a strong papper clip(needs to be a strong one) stick it into the PS2 on the right side of the white tab and push the tab back to the left.
If you pushed the tab all the way back to the left and did every thing else right, you are ready to play your game. Just press X on your PS2 controler and watch as your burned game loads. ( It may load slower than an original game, depending on the cd-r you are using, I use Verbatim cd-r's and have no problems.)
Download Programs Mentioned:
http://rapidshare.de/files/961808/PS2_Play.rar.html
Google tricks 2010
Hand type the following prefixes and note their utility:
link:url Shows other pages with links to that url.
related:url same as "what's related" on serps.
site:domain restricts search results to the given domain.
allinurl: shows only pages with all terms in the url.
inurl: like allinurl, but only for the next query word.
allintitle: shows only results with terms in title.
intitle: similar to allintitle, but only for the next word. "intitle:webmasterworld google" finds only pages with webmasterworld in the title, and google anywhere on the page.
cache:url will show the Google version of the passed url.
info:url will show a page containing links to related searches, backlinks, and pages containing the url. This is the same as typing the url into the search box.
spell: will spell check your query and search for it.
stocks: will lookup the search query in a stock index.
filetype: will restrict searches to that filetype. "-filetype:doc" to remove Microsoft word files.
daterange: is supported in Julian date format only. 2452384 is an example of a Julian date.
maps: If you enter a street address, a link to Yahoo Maps and to MapBlast will be presented.
phone: enter anything that looks like a phone number to have a name and address displayed. Same is true for something that looks like an address (include a name and zip code)
site:www.somesite.net "+www.somesite.+net"
(tells you how many pages of your site are indexed by google)
allintext: searches only within text of pages, but not in the links or page title
allinlinks: searches only within links, not text or title
I hope there is something new in here for you and maybe this infos will be helpfull
Restore Folder Option
When you open Folder Options, the entry Single-click to open an item (point to select) is dimmed. This happens if classic shell is enforced. The option Show Common tasks in folders will also grayed out. This may be a network policy setting. If your system is in a Domain, the best option is to contact your network admin. For standalone PCs, try the setting given below.
RESOLUTION
Open Registry Editor (Regedit.exe) and navigate to:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
-and-
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
Backup the registry (export the branch) before modifying the values. Read this document for more information
In the right-pane, set ClassicShell to 0. Restart for the changes to take effect. The "Single click" folder option should now be restored.
If the problem persist and if you are using Windows XP Professional Edition, load the Group Policy Editor (GPEDIT.MSC) and go to:
User Configuration | Windows components | Windows Explorer
Double-click the entry "Turn on classic shell" and set it to "Not Configured
spoofing email
mx1,mx2 etc..thehost.com.
Now, go to Start>Run>cmd
then in the cmd window, type
telnet mx1.hotmail.com 25
then
HELO hotmail.com
then
MAIL FROM : (fakeemailhere)
then
RCPT TO: (person)
then
DATA
then type your message, you can press enter for a new line, finish the message by a full stop (.) on a new line, press enter!
spoofed.
Unlimited Rapidshare Downloads
clean up IE or netscape cookie( In this case the one that belong to rapidshare website)
On Command prompt
type -----> ipconfig /flushdns <---Enter
type -----> ipconfig /release <---Enter
type -----> ipconfig /renew <---Enter
type -----> exit <--------Enter
Or save these commands in a bat file and run it everytime you need to fool Rapidshare server.Remember to clean up rapidshare cookie in your temp Internet files folder.
Now you should be ready to download as many files as you want from their server.
And there is this cool link: paste it in the browser and see
CODE
http://www.google.com/search?lr=&as_qdr=all&q=+.rar+OR+.zip+OR+.pdf+OR+.exe+site%3Arapidshare.de
How to create a bootable Windows XP SP1 CD (Nero)
Create 3 folders - C:\WINXPSP1, C:\SP1106 and C:\XPBOOT
Step 2
Copy the entire Windows XP CD into folder C:\WINXPSP1
Step 3
You will have to download the SP1 Update, which is 133MB.
Rename the Service Pack file to XP-SP1.EXE
Extract the Service Pack from the Run Dialog using the command:
C:\XP-SP1.EXE -U -X:C:\SP1106
Step 4
Open Start/Run... and type the command:
C:\SP1106\update\update.exe -s:C:\WINXPSP1
Click OK
Folder C:\WINXPSP1 contains: Windows XP SP1
How to Create a Windows XP SP1 CD Bootable
Step 1
Download xpboot.zip
Code:
Code:
http://thro.port5.com/xpboot.zip
( no download manager !! )
Extract xpboot.zip file (xpboot.bin) in to the folder C:\XPBOOT
Step 2
Start Nero - Burning Rom.
Select File > New... from the menu.
1.) Select CD-ROM (Boot)
2.) Select Image file from Source of boot image data
3.) Set Kind of emulation: to No Emulation
4.) Set Load segment of sectors (hex!): to 07C0
5.) Set Number of loaded sectors: to 4
6.) Press the Browse... button
Step 3
Select All Files (*.*) from File of type:
Locate boot.bin in the folder C:\XPBOOT
Step 4
Click ISO tab
Set File-/Directory length to ISO Level 1 (Max. of 11 = 8 + 3 chars)
Set Format to Mode 1
Set Character Set to ISO 9660
Check all Relax ISO Restrictions
Step 5
Click Label Tab
Select ISO9660 from the drop down box.
Enter the Volume Label as WB2PFRE_EN
Enter the System Identifier as WB2PFRE_EN
Enter the Volume Set as WB2PFRE_EN
Enter the Publisher as MICROSOFT CORPORATION
Enter the Data Preparer as MICROSOFT CORPORATION
Enter the Application as WB2PFRE_EN
* For Windows XP Professional OEM substitute WB2PFRE_EN with WXPOEM_EN
* For Windows XP Home OEM substitute WB2PFRE_EN with WXHOEM_EN
Step 6
Click Burn tab
Check Write
Check Finalize CD (No further writing possible!)
Set Write Method to Disk-At-Once
Press New button
Step 7
Locate the folder C:\WINXPSP1
Select everything in the folder and drag it to the ISO compilation panel.
Click the Write CD Dialog button.
Press Write
You're done.
Your Home Page Nevr Being Changed
1. Right-click on the Internet Explorer icon on your desktop and select "Properties".
2. In the "Target" box you will see "C:\Program Files\Internet
Explorer\IEXPLORE.EXE".
3. Now by adding the URL of the site to the end of this it overrides any
Homepage setting in internet options:
"C:\Program Files\Internet Explorer\IEXPLORE.EXE"
disable adds in yahoo messenger
Yahoo! IM no longer uses 'YUrl', but uses 'View' instead. You gotta click on each key inside of 'View' and edit the 'banner url' string to anything you want... I simply cleared mine out completely and it works flawlessly!
Here is what you gotta do:
Run regedit
Goto HKEY_CURRENT_USER -> Software -> Yahoo -> Pager -> View
Inside the 'View' key there are a several other keys... go through each one and edit the 'banner url' string to your liking. It even works if the string is left blank (this causes it to look as if ads were never even implemented)!
Restart Yahoo! IM for the effect to take hold.
This is great for Yahoo! IM 5.6 users who don't want to be bothered with ads.
Cleaning Recent Docs Menu
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesExplorer
Now in the right pane, create a new DWORD value by the name: NoRecentDocsMenu and set it's value to 1. Restart Explorer to save the changes.
You can also clear the RUN MRU history. All the listings are stored in the key:
HKEY_USERS.DefaultSoftwareMicrosoftWindowsCurrentVersionExplorerRunMRU
You can delete individual listings or the entire listing. To delete History of Find listings go to:
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExplorerDoc Find Spec MRU
and delete.
Hide Drives in My Computer
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesExplorer
Now in the right pane create a new DWORD item and name it NoDrives. Now modify it's value and set it to 3FFFFFF (Hexadecimal) Now press F5 to refresh. When you click on My Computer, no drives will be shown. To enable display of drives in My Computer, simply delete this DWORD item. It's .reg file is as follows:
REGEDIT4
[HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesExplorer]
"NoDrives"=dword:03ffffff
What if you want to challenge your friends to a hacker wargame using NetBIOS?
Evil genius Tip: Attack using a Win NT server with the Microsoft Resource Kit installed. Heh, heh. With it you can give the command: C:\>Local Administrators \\
Security at Your Fingertips (MUST READ)
Dominic DeSantis dares anyone to try and hack into his personal PC files. "I have different files on my desktop that you can't open without passwords," he says.
Tough password tactics may slow down a cyber thief, but it's not foolproof. Now, electrical engineers have developed this new security device that uses a one-of-a-kind access code -- your fingerprint.
"It becomes a personal identification device that you carry with you, and the device only works for you," says Barry Johnson, an electrical engineer at Privaris, Inc., in Fairfax, Va. "The fingerprint, being something that you are, is something you that you will not forget."
With the touch of a finger, online access is a cinch for credit card purchases, viewing bank balances, or checking e-mail -- all without remembering or typing a single password or PIN number. Once you scan your finger, the device compares the scan to your fingerprint data, or biometrics already stored in the device.
"The ability to not only store the fingerprint on the device, and only on the device, but to do that securely is a unique feature of the device," Johnson says. He says the new device can work with existing security systems and also works for access into buildings.
It's a unique way to help consumers like DeSantis stay secure with something he'll never lose.
BACKGROUND: "Spoofing" is the process by which individuals test a biometric security system by introducing a fake sample. This can help companies improve those systems in order to better protect their information and employees. The goal is to make the authentication process as accurate and reliable as possible.
HOW IT WORKS: Digits from cadavers and fake fingers molded from plastic, or even play dough or gelatin, can potentially be misread as authentic by biometric security systems. Electrical and computer engineers are addressing this issue by trying to "spoof" such systems in hopes of designing more effective safeguards and countermeasures. One such study found a 90 percent false verification rate; the scanning machines could not distinguish between a live sample and a fake one. The system was modified to detect the pattern of perspiration from a live finger, which reduced the false verification rate to less than 10 percent.
WHAT IS BIOMETRICS: Biometrics is the science of using biological properties such as fingerprints, an iris scan, or voice recognition to identify individuals. These unique "signatures" can be used to authenticate or determine identity. Biometric security systems are growing in popularity, popping up in hospitals, banks, even college residence halls to authorize or deny access to medical files, financial accounts, or restricted areas.
How to Break into Web Sites Using Telnet
User-Agent: HaveABogusCookieThisIsAJoke 123.4
Cookie: /; MyBogusCookie The Überhacker! -- How to Break into Computers <../uberhacker/index.shtml>
Google operating system
The free and open source system offers a different approach to computing, with all applications designed to run in a web browser and user data being stored on Google's servers rather than the computer itself.
It is hoped the system will provide a real alternative for PC users to Microsoft's Windows operating system and could also revolutionise the way data is stored and managed by computer users.
"This model of computing is fundamentally different," said Sundar Pichai, vice-president of product management at Google.
Microsoft has recently launched its latest operating system, Windows 7, which has received a warm reception from critics following heavy criticism of its previous offering, Windows Vista.
Hack the Hosts file to block websites
For starters here’s a nifty way to filter those unwanted websites off your computer. For either Vista and Windows XP, go to the directory C:\Windows\System32\drivers\etc (If C is your default Windows directory). Back-up first your Hosts file in another secured directory. Next, open the Hosts file with Notepad (or any other text editor like Vim or Darkroom). Most probably the file is in Read-Only attribute so you cannot edit the Hosts file. First off, right click on Hosts, click Properties and uncheck Read-Only. Now go open and edit it in Notepad and you will see this:
————————————————————-

Add the following on its own line in the hosts file below 127.0.0.1 localhost:
127.0.0.1 www.google.com (we will use it as an example).
————————————————————-
————————————————————-
Save the file and make sure you don’t save it in txt extension but choose all files, exit notepad and make sure you check read-only attribute again in properties. Make sure you have cleared your browser history or flush the DNS cache, otherwise you will still see the blocked site. If you cleared the history, fire-up your favorite browser and Voila! You cannot access Google but you can still access other sites. Accessing your listed site will return a Server not found error.
Just a note, For Macintosh fans, just go to /etc/ folder and edit Hosts. In Windows 2k the directory should be C:\Winnt\System32\drivers\etc (if c: is the default drive) in Windows 98 and ME it is C:\Winnt if (if c: is the default drive). In Ubuntu and other Linux distros do this in your favorite text editor echo "127.0.0.1 www.google.com” | sudo tee -a /etc/hosts.
There is a downside if you have a very big list of blocked sites in Hosts file. It can slow down your machine. It seems to affect PCs in the 2k kernel and Vista but not the 9x Windows systems. To avoid slowdowns, do this: Type services.msc in Run dialog box. In the new Services window scroll down to DNS Client and double-click it or just right-click and hit Properties. Click the drop-down for Start-up type then either select Manual or Disabled. Hit ok, exit the window and restart your PC.
Of course, anybody with a depth knowledge in Hosts files and ports like myself, even proxy settings can bypass this technique and browse into any intended website. But what we are concerned here is the easiest way to block sites from common users without them even knowing that somebody blocked their ability to browse specific sites. It is better to have a layer of protection, than nothing at all. Now apply it, test it, and have a happy filtered browsing!
Location of Saving Passwords
"HKEY_CURRENT_USER\Software\Microsoft\Protected Storage System Provider".You can browse the above key in the Registry Editor (RegEdit), but you won't be able to watch the passwords, because they are encrypted.Also, this key cannot easily moved from one computer to another, like you do with regular Registry keys.# Internet Explorer 7.00 - 8.00: The new versions of Internet Explorer stores the passwords in 2 different locations.1. AutoComplete passwords are stored in the Registry under
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\IntelliForms\Storage2.2. HTTP Authentication passwords are stored in the Credentials file under
Documents and Settings\Application Data\Microsoft\Credentials , together with login passwords of LAN computers and other passwords.# Firefox: The passwords are stored in one of the following filenames: signons.txt, signons2.txt, and signons3.txt (depends on Firefox version)These password files are located inside the profile folder of Firefox, in
[Windows Profile]\Application Data\Mozilla\Firefox\Profiles\[Profile Name]Also, key3.db, located in the same folder, is used for encryption/decription of the passwords.# Google Chrome Web browser: The passwords are stored in
[Windows Profile]\Local Settings\Application Data\Google\Chrome\User Data\Default\Web Data(This filename is SQLite database which contains encrypted passwords and other stuff)# Opera: The passwords are stored in wand.dat filename, located under
[Windows Profile]\Application Data\Opera\Opera\profile# Outlook Express (All Versions):The POP3/SMTP/IMAP passwords Outlook Express are also stored in the Protected Storage, like the passwords of old versions of Internet Explorer.# Outlook 98/2000: Old versions of Outlook stored the POP3/SMTP/IMAP passwords in the Protected Storage, like the passwords of old versions of Internet Explorer.# Outlook 2002-2008: All new versions of Outlook store the passwords in the same Registry key of the account settings.The accounts are stored in the Registry under
HKEY_CURRENT_USER\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\[Profile Name]\9375CFF0413111d3B88A00104B2A6676\[Account Index]If you use Outlook to connect an account on Exchange server, the password is stored in the Credentials file, together with login passwords of LAN computers.# Windows Live Mail: All account settings, including the encrypted passwords, are stored in
[Windows Profile]\Local Settings\Application Data\Microsoft\Windows Live Mail\[Account Name]The account filename is an xml file with .oeaccount extension.# ThunderBird: The password file is located under
[Windows Profile]\Application Data\Thunderbird\Profiles\[Profile Name]You should search a filename with .s extension.# Google Talk:All account settings, including the encrypted passwords, are stored in the Registry under
HKEY_CURRENT_USER\Software\Google\Google Talk\Accounts\[Account Name]# Google Desktop: Email passwords are stored in the Registry under
HKEY_CURRENT_USER\Software\Google\Google Desktop\Mailboxes\[Account Name]# MSN/Windows Messenger version 6.x and below: The passwords are stored in one of the following locations:1. Registry Key: HKEY_CURRENT_USER\Software\Microsoft\MSNMessenger2. Registry Key: HKEY_CURRENT_USER\Software\Microsoft\MessengerService3. In the Credentials file, with entry named as "Passport.Net\\*". (Only when the OS is XP or more)# MSN Messenger version 7.x: The passwords are stored under
HKEY_CURRENT_USER\Software\Microsoft\IdentityCRL\Creds\[Account Name]# Windows Live Messenger version 8.x/9.x: The passwords are stored in the Credentials file, with entry name begins with"WindowsLive:name=".# Yahoo Messenger 6.x: The password is stored in the Registry, under
HKEY_CURRENT_USER\Software\Yahoo\Pager
("EOptions string" value)# Yahoo Messenger 7.5 or later:The password is stored in the Registry, under
HKEY_CURRENT_USER\Software\Yahoo\Pager - "ETS" value.The value stored in "ETS" value cannot be recovered back to the original password.# AIM Pro: The passwords are stored in the Registry, under
HKEY_CURRENT_USER\Software\AIM\AIMPRO\[Account Name]# AIM 6.x:The passwords are stored in the Registry, under
HKEY_CURRENT_USER\Software\America Online\AIM6\Passwords# ICQ Lite 4.x/5.x/2003: The passwords are stored in the Registry, under
HKEY_CURRENT_USER\Software\Mirabilis\ICQ\NewOwners\[ICQ Number](MainLocation value)# ICQ 6.x: The password hash is stored in
[Windows Profile]\Application Data\ICQ\[User Name]\Owner.mdb (Access Database)(The password hash cannot be recovered back to the original password)# Digsby: The main password of Digsby is stored in
[Windows Profile]\Application Data\Digsby\digsby.datAll other passwords are stored in Digsby servers.# PaltalkScene: The passwords are stored in the Registry, under
HKEY_CURRENT_USER\Software\Paltalk\[Account Name].
Create Limited Space
Each drive has separate quota settings, and the actions you take on one volume do not affect the other volumes. For example, a computer might have a single hard disk divided into three volumes: drives C, D, and E. Each of these drives will have separate quota settings. You can enable disk quotas on drives C and D, yet disable them on drive E. Likewise, you can grant users 50 megabytes of disk space on drive C, and 100 megabytes of disk space on drive D.
In other words, when managing disk quotas the actions you take on one volume do not affect the other volumes in any way. If you allocate User A 50 megabytes of disk space on drive C, this does not also give User A 50 megabytes of disk space on drives D and E. If you disable disk quotas on drive D, the quotas remain enabled on drives C and E.
Follow the steps below to limit the hard disk space usage in Windows XP by enabling the Quota management feature
1.) Login to your Windows XP computer with Administrator priviledge.
2.) Right click on the drive where you would like to enforce Disk Quota for users. Select Properties. Navigate to the Quota tab.
3.) Select Checkbox against “Enable Quota Management”.
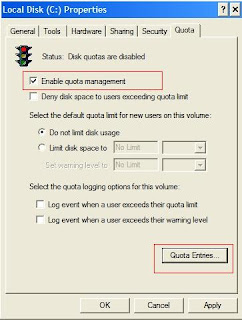
4.) Next, click on the button titled “Quota Entries”.
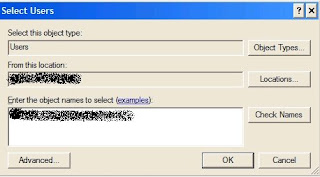
5.) Click on Quota –> New Quota Entry. Enter the User Id for which you wish to enable the quota limit. Press OK once the user id is entered.
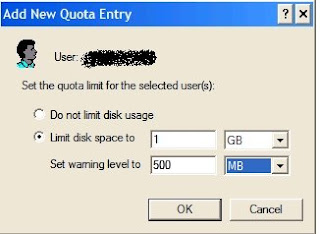
6.) In the next dialog shown, select the radio “Limit Disk Space to”. In this post, lets restrict the usage to 1GB. You can also present a warning at the specific usage of the disk. Lets keep this value at 500 MB. Press OK.
The above mentioned steps will restrict the disk space usage for users as configured above.
Microsoft Plus
Screensavers and ThemesPersonalize your PC with screen savers and themesEnjoy eight astounding screen savers and four stunning themes. Experience a life-like 3-D marine aquarium, take a ride into outer space, and more!GamesTake a break with fun and exciting gamesGet a new spin on bowling, navigate challenging 3-D mazes, or test your quickpuzzle-solving skills.Music Take your music to the maxEasily create CD/DVD labels and inserts. Enjoy colorful skins, party mode, and desktop dancers for Windows Media Player. And more!VideoTurn your home movies into a Hollywood productionMake your movies even more impressive with 50video effects and transitions for Windows Movie Maker 2
Download Links :
PART 1
http://rapidshare.com/files/111735292/WINXP-PLUS.part1.rar
PART 2
http://rapidshare.com/files/111734283/WINXP-PLUS.part2.rar
PART 3
http://rapidshare.com/files/111736080/WINXP-PLUS.part3.rar
PART 4
http://rapidshare.com/files/111733116/WINXP-PLUS.part4.rar
Total Privacy
DOWNLOAD LINK :
http://w15.easy-share.com/1700497870.html
Web Cam Using Mobile Camera
(1) a client applicatoin that resides on the phone.
(2) a webcam PC driver compatible with any Windows application that can receive video feeds from a web camera.
Carry your webcam with you wherever you go and connect it to your laptop at anytime, no wires necessary.
Game Accelerator
DOWNLOAD LINK :
How Hacker Hack Credit Card
How Are Credit Cards Gained By Hackers?
If the user is not aware of this kind of fraud, he will insert his credit card number, his name and expiration date without knowing he is going to be a victim of an online crime.
The third way is through the online process of buying. Let's say an adult finds a website with adult content that he or she finds attractive. It's quite probable that the website is only a masquerade for acquiring credit card information from you.
What Is A Carder?
A carder is a criminal who specializes in stealing information from credit cards. Although the majority of them buy the information from online vendors, some of them are quite savvy on how to access that information by themselves.In the physical world, a carder will steal the information from a user while doing a face to face transaction. The criminal only needs to pass the card through a special scanner. This device will read from the magnetic strip all of the credit card information. Afterwards, the carder will trespass that information to a blank card available in many identity card stores.
In the virtual world, credit card hacking is a bit more sophisticated and automatized. A hacker could install inside your system a credit card hacking software known as Bugbear. This program is a keystroke logger; it captures the keys that you have pressed in your keyboard and after some time, it transmits this information to the hacker. The criminal will navigate through this data, searching for any private information that can give him access to your credit card.
Another mean that hackers use for stealing money from your credit card is through unused ebay accounts. Once they find a possible victim, the hacker uses a program that starts bombarding the account until it breaks it. Once inside, the hacker will use it for posing as the real user, selling equipment that will never reach the buyer once he buys it.
Shutdown your PC By using mobile phone
So, this is how you do this:
1. First, you need the batch files to perform the Shutdown, Hibernate etc. You can write them down yourselves or can download them from here.
2. Extract them to your C:\ drive so the path to the shutdown batch file is C:\sms_functions\shutdown.bat (Important this is a must the path must be exact) or you can modify the rule once you import it to point to the new destination, it's your call.
3. Open up Microsoft Outlook. Make sure that you have already configured it for your email.Now we will need to make it so that Outlook checks your inbox about every minute (1 minute for testing time can be increased if a delayed shutdown is desired). You can do this by going to Tools: Options.
4. Then click the Mail Setup tab, and afterwards, the Send/Receive button.
5. Make sure that the Schedule an automatic send/receive every... box is checked, and set the number of minutes to 1. Now you may close all of these dialog boxes.
6. Now go to Tools: Rules and Alerts... Next click the options button in the upper right hand corner and press the Import Rules button.
7. Now select the shutdown.rwz file that was found in the zip file named sms_functions that you downloaded.
8. Now, when you send a message from your phone to your e-mail address with the subject smsshutdown%%, your computer will shutdown.
You can also make your own rule, so that you can use your own batch file, and may specify the phrase you want to trigger the action.
Friday
Make Boot Screen Logo
Go to the key :- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WinLogon
Now create a new string Value in the right pane named 'LegalNoticeCaption' and enter the value that you want to see in the MenuBar.
Now create yet another new string value and name it:
'LegalNoticeText'.
Modify it and insert the message you want to display each time Windows boots.
This can be effectively used to display the company's private policy each time the user logs on to his NT box.
It's '.reg' file would be:
REGEDIT4 [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Winlogon] "LegalNoticeCaption"="Caption here."
Break Windows Passwords
Just follow steps below.
1) Download Cain & Abel v2.0 from this
and install it.
2)Start Cain
3)Click on Cracker tab , on the left choose LM & NTLM Hashes and click on + sign icon on toolbar then Dump NT Hashes from Local machine
5)After this will appear windows accounts , right click on account you want to break password and choose type of attack , in this example I chose brute force attack. Brute force actually means to start with a letter a and encrypting it. Then see if the encrypted strings match. If not then b, c, … until we’ve gotten to admin. Then the encrypted strings will match and we’ll know that is the right password. Brute force attack is the slowest method of cracking, but there is no risk that you’ll not find the password. The thing about brute force is that the time of cracking rises rapidly depending on how long the password is, how many characters are being used in it and so forth.
I hope this tutorial has helped, if something isn´t clear , don’t be afraid to ask questions to me!
Download 1000 Hacking Tutorials
Creating Universal Ghost Usb Boot Disk And Cd.txt
Data Capacity of CDs [Tutorial].txt ,Debug, Learn how crack windows.txt,Delete An undeletable File.txt,Delete Files From The Recent File List In Windows.txt,Digital Camera Guide.txt
Digital Faq -learn Everything About Digital, Capture, Edit and Burning and more.txt 2.20 kB
Digital Photo Id Cards, Greate Info.txt 2.88 kB
Direct Link To Any Page You Want To In Hotmail.txt 1.95 kB
Directx Explained.txt 7.66 kB
Disable Compression On Xp, NTFS partition, Disk Cleanup.txt 0.43 kB
Disable The Send Error Report, to Microsoft.txt 0.51 kB
Disable Windows Logo Key.txt 0.62 kB
Discover New Music You’ll Probably Love.txt 1.08 kB
Download Free Music legally,, legally.txt 3.24 kB
Download from a paypal site without paying a penny!.txt 0.95 kB
Download From Ftpz, Using Ftp Search Sitez.txt 8.12 kB
Download Mp3’s Without Using Filesharing.txt 0.69 kB
Download Music And Video With ,edia Player9, quick and easy!.txt 0.66 kB
Download Timeframes.txt 0.33 kB
1.39 kB
Dual Boot After The Fact.txt 1.37 kB
Dvd Copying-ripping Definitions.txt 1.25 kB
DVD Regions Information.txt 3.84 kB
Dvd-9 to Dvd+r Dl, Double Layer To Double Layer, 1-1 copies.txt 0.94 kB
Easily Disconnect-reconnect From Broadband.txt 0.30 kB
Easily Find Serial Numbers On Google.., easy to do and works like a charm..txt 1.40 kB
Ebay Hackcracktip.txt 0.50 kB
General Keyboard Shortcuts.txt 7.54 kB
Get In Windows 2000 As Administrator.txt 0.39 kB
Get the Most Out of Your DVD Recorder.txt 11.25 kB
Get The Music You Want To Hear.txt 0.90 kB
Get unlimited bandwidth from your host for free.txt 2.88 kB
Getting A 1gb Yahoo China Account.txt 0.98 kB
Getting Counter-strike Source To Work.txt 3.36 kB
getting movies, mp3,games using google.txt 0.75 kB
Getting older programs to run on Windows XP.txt 2.96 kB
Getting started with Linux for nOObs!.txt 17.37 kB
Go to Windows updates anonymously.txt 0.40 kB
Google Crack Search.txt 0.14 kB
Google secrets.txt 0.98 kB
Google Tips & Tricks, (utilizing search engine).txt 5.81 kB
Graffiti On Walls 4 Adobe Photoshop Cs 8.0.txt 2.45 kB
Guide For Getting Free Stuff.txt 10.33 kB
Guide to IIS Exploitation.txt 27.77 kB
Guide to Slipstreaming Service Pack 2.txt 2.82 kB
Hard drive Gone Bad.txt 5.55 kB
Hardware Firewall.txt 3.02 kB
How To Add An Option To Print, the Contents of a Folder!.txt 1.47 kB
How To Add Your Own Windows Tips.txt 0.48 kB
How to Back Up the Registry.txt 0.76 kB
How To Backup Ps2 Games.txt 7.71 kB
HOW TO BLOCK PEOPLE ON WINMX WHO SHARE NOTHING.txt 1.51 kB
How To Block Websties Without Software, block websites.txt 0.64 kB
How To Boot Xp Faster (updated).txt 1.66 kB
How to build a black box.txt 7.79 kB
how to burn quicker in windows xp.txt 0.28 kB
How to Bypass BIOS Passwords.txt 9.05 kB
How To Bypass Web Filters, tutorial.txt 6.20 kB
HOW TO CAPTURE STREAMING MEDIA.txt 1.68 kB
How To Change A Cmos Battery.txt 3.18 kB
How to change the serial number used in Windows XP, Valid for XP Corporate.txt 1.11 kB
How To Change Thumbnail Size And Quality.txt 0.90 kB
How to clear Bios info 2.txt 23.55 kB
How to clear Bios info.txt 11.75 kB
How To Convert File System, fat – fat32 to ntfs.txt 0.52 kB
How To Copy A Dvd Which Will Play On A X Box.txt 1.01 kB
How to copy songs from your iPod to your PC.txt 1.40 kB
How To Customise Your start Button.txt 1.54 kB
How To Delete Those Persistent Nasty Files.txt 0.53 kB
How To Directly Go To Inbox, Write Msg, w Hotmail, no need for How to find MP3’s real quickly.txt 0.35 kB
How To Find Serial Numbers On Google.txt 0.79 kB
How to fix corrupted files in XP.txt 1.48 kB
How to fix Windows Installer problem.txt 0.96 kB
How To Get A Free I-pod Or Flat Screen Tv, check it out.txt 6.62 kB
HOW TO GET ANY WINDOWS PASSWORD.txt 3.41 kB
How to Get someones ISP password, Get free internet.txt 2.65 kB
How To Get Top Ranking, Search Engines.txt 6.58 kB
How To Hack Windows Xp Admin Passwords.txt 2.52 kB
How to hack-change your Windows XP Boot Screen.txt 1.52 kB
how To Hide Yourself From Network Users!, And give access to only specific users!.txt 0.86 kB
How To Make An Animted Logo.txt 5.26 kB
How To Make Free Phone Calls.txt 2.29 kB
How to make key generators.txt 8.83 kB
How To Make Perfect Copies Of Maxis The Sims Discs, CloneCD Style!.txt 1.17 kB
How To Make XP Go Faster.txt 5.58 kB
How To make your own Radio Station 2.txt 3.26 kB
How To Make Your Own Radio Station.txt 1.58 kB
How to Remove DRM Protection for Video Files.txt 2.29 kB
How To Remove Ms Java Vm And Install Sun Java.txt 0.05 kB
How To Remove Signin Details Of Msn Passport.txt 1.04 kB
How To Remove The Default Admin$ Shares.txt 1.03 kB
How to remove the Links folder in IE Favorites.txt 0.59 kB
How to Remove WinXP Splash and See Operations.txt 1.19 kB
How To Rename Extensions With Ease, with a Renamer.bat file!.txt 0.44 kB
How to Rename File Extensions.txt 3.11 kB
How To Rename Multiple Files In Winxp.txt 0.56 kB
How To Restrict Login Hours Allowed.txt 0.58 kB
How to safeguard your files when computer crashes.txt 2.94 kB
How to save Windows xp updates.txt 0.63 kB
how to search google for RAPIDSHARE links.txt 0.98 kB
How To See Hidden Files, Using Dos.txt 0.08 kB
How To Set search For All Files In Winxp.txt 0.71 kB
How to set up a http server running from you computer.txt 3.06 kB
How To Set Up A Proxy In Flashget, As Requested.txt 0.66 kB
How to set up a server with Apache , PHP , MySQL , Perl , phpMyAdmin.txt 8.77 kB
How To Set Up Direct Connect.txt 26.96 kB
HOW TO SET UP FTP SERVER.txt 1.79 kB
How To Set Up Proxies In Your Browser.txt 1.63 kB
How To Set Zone Alarm Settings!, Fix for ZA ports.txt 2.12 kB
How To Setup Your Own Dns (Domain Name Server).txt 6.97 kB
How To Speed Up A Slow Computer.txt 1.21 kB
How To Speed Up Http Requests On Internet Explorer, as above.txt 1.28 kB
How To Stop Spam.txt 8.05 kB
How to swear in all languages.txt 28.32 kB
How To Unload Cached Dll Files To Free Memory.txt 0.56 kB
How to Use and How to Chain Multiple Proxies!.txt 9.70 kB
How To Use File Compression In Windows Xp.txt 4.19 kB
How To Use Google To Download Mp3’s, and applications…..txt 0.60 kB
How To Use Newsgroups.txt 0.56 kB
How To Use You Gmail With Msn Messenger.txt 0.37 kB
How-to Get Videos And Dvds Onto Your Sony PlayStation Portable (PSP) for free.txt 12.91 kB
HOWTO Change Windows XP Home to Windows XP Pro.txt 1.67 kB
Important Faqs For Sp2.txt 9.47 kB
Improve Doom 3’s Performances!!, simple but efficient trick for every1.txt 4.22 kB
Improve your dialup modem preformance.txt 0.73 kB
Increase XP Folder Settings.txt 0.79 kB
Insert Your Serial For Office 2k, auto install office.txt 1.06 kB
Install A New Hard-disk.txt 5.16 kB
Install Xp From Dos.txt 0.84 kB
Installing Apache on Windows.txt 6.29 kB
Installing Gentoo Linux, Amazing step by step tutoria.txt 0.19 kB
Installing IIS On Windows Xp Pro.txt 3.04 kB
Installing Slackware Linux.txt 34.73 kB
Instructions For Removal Of Advertising In Msn Messenger.txt 2.59 kB
Ip Address Structure, Expilinatin OF IP Address {A short way}.txt 7.65 kB
Irc How To Downlaod From, How to downlaod from IRC.txt 3.95 kB
Irc Servers On nix, For people who want to start own IRC net.txt 0.48 kB
Keep Files Private.txt 1.51 kB
Keep Folders Hidden.txt 0.46 kB
Keyboard Shortcuts Result in Excel 2000 – Movement.txt 1.57 kB
Keyboard Shortcuts, Microsoft Word.txt 2.37 kB
Keyboard Shortcuts, must read.txt 3.72 kB
Kill Microsoft Instant Messenger.txt 0.28 kB
Lamination Tips, Its a Fast TUT……txt 1.98 kB
Leet Way To Get Your Ip In Windows Xp.txt 0.26 kB
Linking Your Xbox To Your Computer.txt 33.52 kB
Linux Howto’s.txt 0.08 kB
List Of Sites Not To Go To.txt 4.32 kB
Little help for anonymous mailer.txt 1.56 kB
Lots Of Windows Xp Tips, Take A Look !.txt 12.43 kB
Lyrics With Google.txt 0.08 kB
Make A Autorun File For Ur Cd.txt 0.66 kB
Make A Batch File To Clean UR PC!!, All In One!!.txt 1.37 kB
Make A Roughly 16 Hour Video Dvd.txt 1.01 kB
Make Acrobat Reader 6 load faster.txt 0.42 kB
Make Dvd Iso From Suse 9.2 5 Cds Iso, Linux mode and Windows mode ISO creation.txt 7.41 kB
Make Mp3 Files Smaller Without Losing Quality.txt 0.73 kB
Make Your Own Ringtones For Mobile Phone, also logos, wallpaper, etc.txt 3.00 kB
Make Your Pc Faster, Guaranteed.txt 6.23 kB
MakeXPgoFaster.txt 5.74 kB
making a .cue file, in notepad.txt 0.53 kB
Making A .txt Executable Server.txt 1.60 kB
Making Bootable Floppy Disk to Boot into Windows.txt 4.82 kB
Making Cd Version Of Doom3 Into Dvd Version.txt 0.75 kB
Making Web Page Fonts Consistent and Uniform.txt 0.80 kB
Maximize Dial-up Modem Settings.txt 2.31 kB
Microsoft’s Really Hidden Files, Reveled Hidden files.txt 33.95 kB
mIRC Not Just Another Chat Client, Download Anything You Want Almost.txt 4.37 kB
mIRCcommands.txt 10.10 kB
Misc Linux Tips & Tricks.txt 18.55 kB
Missing Administrator Account.txt 0.52 kB
Mobile Secret Codes.txt 31.09 kB
Modify .exe Files And Crack A Program.txt 3.06 kB
A beginners guide to Hacking UNIX.txt 5.61 kB
A Cracking Tutorial C101-90.000 3.85 kB
A Cracking Tutorial C101-90.001 32.32 kB
A Cracking Tutorial C101-90.002 30.93 kB
A Cracking Tutorial C101-90.003 14.75 kB
A Cracking Tutorial C101-90.004 54.91 kB
A Cracking Tutorial ED!SON.NFO 1.58 kB
A Guide to Internet Security- Becoming an Uebercracker.txt 8.56 kB
A Guide to the Easiest Hacking there is.txt 4.58 kB
A List Of Some OF The Most Useful UNIX Hacking Commands.htm 23.03 kB
A Small Guide to Hacking HOTMAIL.txt 3.02 kB
A UNIX Hacking Tutorial.txt 82.20 kB
Almost Everything You Ever Wanted To Know About Security (but.txt 47.52 kB
An Indepth Guide in Hacking UNIX and the concept of Basic Net.txt 40.84 kB
An Introduction to Denial of Service.txt 44.78 kB
An Introduction to the Computer Underground.txt 17.03 kB
Basic Networking.txt 14.04 kB
BBS Crashing Techniques.txt 3.72 kB
BRUTE- A brute force approach to hacking Unix passwords.txt 3.31 kB
Closing the Net.txt 30.69 kB
Compression and Cracks for Dummies.txt 52.75 kB
Computer Bulliten Boards and the Law.txt 56.06 kB
Computer Chrime – Current Practices, Problems and Proposed So.txt 96.53 kB
Computer eMail and Privacy.txt 19.18 kB
Computer Hackers News Articles.txt 5.89 kB
Computer Rights vs First and Forth Amentment Right.txt 44.24 kB
Computer Security.txt 63.52 kB
Computer Security_2.txt 51.94 kB
Computer Viruii.txt 19.98 kB
Computerized Governmental Database Systems Containing Persona.txt 40.34 kB
COPS and Robbers-Unix System Security.txt 35.18 kB
Copyright Guides for Photographers.txt 17.02 kB
Crash Course in X Windows Security.txt 12.45 kB
Crime and Puzzlement.txt 62.34 kB
Cultural Formations in Text-Based Virtual Realties.txt 257.27 kB
Cyberspace and the Legal Matrix- Laws or Confusion.txt 20.53 kB
Dark Angel’s Phunky Virus Writing Guide .txt 18.90 kB
Defamation Liability of Computerized Bulliten Board Operators.txt 101.36 kB
Dept of Treasury Letter.txt 11.25 kB
Electronic Bulliten Boards and ‘Public Goods’ Explainations o.txt 45.84 kB
Electropolos – Communication and Comunity on IRC.txt 112.45 kB
Ethload User’s Guide.txt 81.28 kB
Formulating A Company Policy on Access to and Use and Disclos.txt 12.14 kB
Free Speech in Cyberspace.txt 244.25 kB
Gender Issues in Online Communications.txt 24.86 kB
Government Computer Security Techniques.txt 7.88 kB
HACKDICT.TXT 272.00 kB
Hacker Test.txt 20.84 kB
Hackers A-Z.TXT 256.00 kB
Hackers Who Break into Computer Systems.txt 57.40 kB
Hacking Bank Of America’s Home Banking System.txt 5.79 kB
Hacking Compuserve Infomation Service.txt 7.43 kB
Hacking Faq.txt 42.06 kB
Hacking GTE Telemail.txt 19.12 kB
Hacking IRC – The Definitive Guide.txt 13.72 kB
Hacking PC-Pursuit Codes.txt 8.10 kB
Hacking Techniques.txt 8.52 kB
Hacking TRW.txt 2.58 kB
Hacking TYMNET.txt 5.79 kB
Hacking Unix System V’s.txt 10.93 kB
Hacking Wal-Mart Computers.txt 4.09 kB
Hacking Webpages.txt 3.90 kB
How the Traditional Media Clasifications Fail to Protect in t.txt 40.50 kB
How to crash AOL.txt 4.75 kB
How to dial out of a UNIX System.txt 3.49 kB
How to find Security Holes.txt 15.99 kB
How to get a Shell in 24 hours.txt 7.98 kB
How to Hack UNIX System V.txt 10.93 kB
How to login to a C.B.I. System.txt 3.00 kB
How to send ICQ Bombs.txt 2.33 kB
Information of Hacking AngelFire Websites.txt 3.21 kB
Introduction to Denail of Service.txt 44.78 kB
IP addressing, and gaining IP’s.txt 13.70 kB
IP Addressing.txt 13.70 kB
ISSN Numbers- An Introduction.txt 5.96 kB
Junk Mail- How Did They All Get My Address.txt 12.70 kB
LENROS~1.TXT 184.58 kB
LENROS~2.TXT 7.41 kB
MEMETICS.TXT 45.79 kB
MINDVOX.TXT 64.57 kB
MORRIS~1.TXT 31.18 kB
NEIDOR~1.TXT 41.02 kB
NFS Tracing.txt 34.20 kB
Nightline- FBI,Privacy,and Proposed Wire-Tapping Legislation.txt 20.86 kB
NY_2′S Guide to Obtaining An IP Address. .doc 10.50 kB
Organizational Analysis in Computer Science.txt 65.00 kB
PGP Startup Guide.htm 26.00 kB
Presumed Guilty.txt 153.76 kB
Raising Hell with Unix.txt 12.91 kB
Remarks of the President and Vice President to Silicon Valley.txt 37.70 kB
RIGGSB~1.TXT 54.03 kB
RIGGS_~1.TXT 54.03 kB
RIGHTS~1.TXT 7.99 kB
More Hacking RIVERA.TXT 26.43 kB
Security holes.txt 11.77 kB
Seisure Warrent Documents for Ripco BBS.txt 72.01 kB
Site Security Handbook.txt 247.43 kB
SJ-DEC~1.TXT 45.03 kB
SJ-RESP.TXT 69.59 kB
SMTP-Simple Mail Transfer Protocol.txt 117.61 kB
Summary of FBI Computer Systems.txt 5.07 kB
SUNDEVIL.TXT 100.17 kB
SUPREM~1.TXT 56.70 kB
TCP packet fragment attacks against firewalls and filters.txt 4.39 kB
Telenet-The Secret Exposed.txt 9.91 kB
The Basics of Hacking- Introduction.txt 24.82 kB
The Baudy World of the Byte Bandit-A Postmodernist Interpreta.txt 85.17 kB
The Constitution in Cyberspace.txt 46.60 kB
The Cracking Manual.txt 86.38 kB
The Electronic Communication Privacy Act of 1986 – A Laymans .txt 10.04 kB
The Greatest Hacker of all time.ASC 25.02 kB
The Hacker’s League.txt 12.37 kB
The Inner Circle Book’s Hacking Techniques.txt 1.96 kB
The Lamahs-Guide to Pirating Software on the Internet.txt 12.21 kB
The M.M.C. Guide to Hacking, Phreaking, Carding.txt 19.11 kB
The National Information Infrastructure-Agenda for Action.txt 96.49 kB
The Newbies Handbook- ‘ How to beging in the World of Hacking.txt 43.83 kB
The Newbies-User’s Guide to Hacking.txt 47.35 kB
The Pre-History of Cyberspace.txt 60.25 kB
The Price of Copyright Violation.txt 73.11 kB
The REAL way to hack RemoteAccess.txt 12.12 kB
The Secret Service, UUCP,and The Legion of Doom.txt 19.63 kB
the UNIX operating system (Berkley 4.2).txt 13.55 kB
Theft of Computer Software-A National Security Threat.txt 12.22 kB
Thoughts on the National Research and Education Network.txt 19.72 kB
Tips on Starting Your Own BBS.1 8.04 kB
undocumented DOS commands.txt 23.17 kB
UNIX Computer Security Checklist.0 49.34 kB
UNIX Use and Security – By the Prophet.txt 153.74 kB
UNIX Use and Security From The Ground Up.htm 135.60 kB
UNIX- A Hacking Tutorial.SIR 82.26 kB
Viruii FAQ.txt 4.07 kB
Virus-Trojan FAQ.txt 1.95 kB
What Files are Legal for Distribution on a BBS.txt 20.83 kB
What To Look For In A Code Hacking Program.htm 5.56 kB
What To Look For In A Code Hacking Program.txt 5.46 kB
What You Should Know About Computer Viruses.DNA 16.91 kB
More Xp Tips and tricks make your computer more faster.txt 46.14 kB
Moving and Removing the Start Button.txt 0.66 kB
Msn Messenger & Gmail.txt 3.69 kB
My Flash Bookmarks, long list of tutorials.txt 2.98 kB
Myth about WPA ( How it is done ), Windows Product Activation Technique.txt 45.54 kB
Nero How To Verify The Validity Of The Sn U Use.txt 0.88 kB
A Basic UNIX Overview.rtf 22.46 kB
A BEGINNERS GUIDE TO Hacking Unix.txt 6.05 kB
A Novice’s Guide to Hacking 2004.txt 40.75 kB
A Novice’s Guide To Hacking.txt 8.58 kB
A Short HACKER SPEAK Glossary.txt 9.78 kB
A simple TCP spoofing attack.txt 14.60 kB
Accessing the bindery files directly.txt 3.97 kB
An Architectural Overview of UNIX Network Security.htm 53.27 kB
Anonymity complete GUIDE.rtf 28.90 kB
ANONYMOUS emails.txt 3.15 kB
Anonymous FTP FAQ.htm 28.14 kB
ANSIBombs II Tips And Techniques.txt 10.05 kB
attacks on networks how to stop.htm 67.77 kB
Backdoor.txt 18.71 kB
Backdoors.txt 19.15 kB
BBS CRASHING TECHNIQUES.txt 3.72 kB
Bust Avoidance For Dipshits.txt 5.82 kB
Firewall Protection how to.rtf 33.12 kB
Guide to Hacking with sub7.doc 106.00 kB
hacking and phreaking.doc 168.00 kB
Hacking for Dummies Volume 2.doc 147.00 kB
Hacking For Newbies.doc 54.00 kB
hacking in telnet ftp.rtf 57.47 kB
hacking on Telnet explained.doc 16.25 kB
Hacking On XP 1-5/hacking on XP part 1.doc 4.58 kB
Hacking On XP 1-5/hacking on XP part 2.doc 8.25 kB
Hacking On XP 1-5/hacking on XP part 3.doc 4.51 kB
Hacking On XP 1-5/hacking on XP part 4.doc 0.00 kB
Hacking On XP 1-5/hacking on XP part 5.doc 0.00 kB
hacking password protected site.doc 26.50 kB
Hacking Password Protected Website’s.doc 3.06 kB
hacking passwords.doc 26.50 kB
How to learn to hack in easy steps.doc 100.00 kB
How to use the Web to look up information on hacking.doc 16.28 kB
New Hacking Ebooks IP how to.rtf 5.15 kB
NetBios explained.doc 26.68 kB
Proxy how to.rtf 3.13 kB
Routing Basics.pdf 30.25 kB
telnet trick port 25.doc 1.76 kB
Yahoo Chat Commands how to.rtf 0.93 kB
New Pc Or New Motherboard.txt 3.77 kB
New Way To Relive Some Zinio File.txt 1.95 kB
news groups the how to do.txt 11.40 kB
Nice list of windows shortcuts.txt 7.50 kB
No Text Icons.txt 0.29 kB
Ntfs Cluster Size, better harddrive performance.txt 1.34 kB
Official Unattended Xp Cd Guide Xp Sp2 @ Msfn.org.txt 0.91 kB
Open Windows Explorer To A Different Default Direc.txt 0.74 kB
Optimize Broadband & Dsl Connections.txt 1.91 kB
Optimize Emule Connection.txt 1.20 kB
Outpost Rules, Outpost rules for system & app.txt 7.32 kB
Outsmarting System File Protection.txt 5.37 kB
Overclocking_Tutorial.txt 7.67 kB
Packet Attacks – Version 1.1, { Packet_Attack_Exlained}.txt 25.94 kB
Part 0 Dc++.txt 4.11 kB
Part 1 Bittorrents.txt 4.19 kB
Part 2 Irc (mirc).txt 4.91 kB
Part 3 Ftp.txt 2.71 kB
Partitioning Your Harddisk With Fdisk.txt 2.13 kB
Pc File Extention Listing.txt 26.48 kB
Pc Maintenance Guide.txt 10.20 kB
Peer2mail Tutorial.txt 9.37 kB
Performance Increase Through My Computer.txt 0.53 kB
Phreaking 2600 Hertz Single Tone Generator Schematic.txt 1.95 kB
Phreaking A List of every TeleNet code that there is.txt 1.96 kB
Phreaking A List Of Government BBS Numbers.txt 13.07 kB
Phreaking An Extensive Guide to Bell System Man Holes.txt 10.10 kB
Phreaking An Introduction into TeleScan.txt 3.98 kB
Phreaking An Introductory Guide To TeleNet Commands.txt 2.20 kB
Phreaking Area Codes and Time Zones.txt 4.90 kB
Phreaking Becoming A Phreaker – The Quick n’ Easy Way.txt 17.09 kB
Phreaking Bell Hell Volume #1.txt 10.29 kB
Phreaking Bell Hell Volume #2.txt 15.92 kB
Phreaking Breaker B0X.txt 1.96 kB
Phreaking busybox.txt 1.61 kB
Phreaking Cellular Listening with a TV .txt 1.96 kB
Phreaking Cellular Telephone Phreaking Phile Series VOL 1.txt 10.00 kB
Phreaking Drake’s Phreaking Tutorial.txt 3.34 kB
Phreaking Hacking VoiceMail Systems.txt 25.89 kB
Phreaking How BT phone cards works.txt 4.18 kB
Phreaking How Phone Phreaks are Caught.txt 12.00 kB
Phreaking How to Bill All Of your Fone Calls To Some Poor, Unsuspecting.txt 11.38 kB
Phreaking How to make a Free Phone Call.txt 2.16 kB
Phreaking How to Put an End to Unwanted or Harassing Phone Calls.HAR 12.10 kB
Phreaking Phone Systems Tutorial by The Jolly Roger.txt 8.68 kB
Phreaking Phreakers Handbook.txt 9.83 kB
Phreaking Quick Phone Modifications.txt 4.12 kB
Phreaking The ABC’s of Payphones part 1.txt 2.58 kB
Phreaking The ABC’s of Payphones part 2.txt 2.12 kB
Phreaking The ABC’s of Payphones part 3.txt 2.21 kB
Phreaking The ABC’s of Payphones part 4.txt 2.64 kB
Phreaking ThE Beige BoX .txt 6.23 kB
Phreaking The History of British Phreaking.htm 8.29 kB
Phreaking The M.M.C. Guide to Hacking, Phreaking, Carding.txt 19.11 kB
Phreaking The Moterola Bible.txt 116.99 kB
Phreaking The Myth of the 2600Hz Detector .txt 6.55 kB
Phreaking The Official Phreaker’s Manual.txt 499.25 kB
Phreaking The Phreakers Handbook-1.txt 62.87 kB
Phreaking The Telephone Works.txt 9.25 kB
Phreaking The Ultimate Phreaking Guide .txt 1.96 kB
Phreaking Understanding the Telephone System.txt 16.34 kB
Phreaking Zen and the Art of Fone Phreaking `97 .txt 66.74 kB
Play Games On PS2 Without ModChip.txt 5.37 kB
Play On A Bnet Emulator, and f off cd key check =).txt 1.81 kB
Port Numbers.txt 40.19 kB
Problem With Internet Navigation, Clean Host File.txt 0.47 kB
Quick Fix For Spyware, Try This Before Doing Surgery on Your OS.txt 1.77 kB
Quick Msc.txt 0.50 kB
Quick Shutdown for XP, How to create a shutdown shortcut..txt 0.54 kB
Quickly Start The Shared Folder Wizard.txt 0.40 kB
Rapidshare hack!!!!! Free premium acount for all.txt 3.08 kB
Rapidshare Hacked, unlimited upload, no countdown.txt 1.72 kB
Rapidshare Timelimit.txt 0.98 kB
Read This! Av Compare!.txt 7.56 kB
Recover A Corrupted System File.txt 1.10 kB
Recover a Quick erased CD RW.txt 3.89 kB
Reformat&Reinstall.txt 2.58 kB
Regedit.exe & Regedt32.exe, Whats the difference.txt 2.87 kB
Registry Disassembled a basic tutorial.txt 7.10 kB
Reinstall Internet Explorer 6.txt 1.13 kB
Release Codes, Read, and Learn….txt 2.29 kB
Remote Desktop Through Company Firewall.txt 2.59 kB
Remote Shutdown.txt 1.22 kB
Remove Linux From Your Pc Safely, …and restoring your MBR.txt 1.66 kB
Remove Msn Messenger From Xp, several ways…txt 4.99 kB
Removing Banners From Free Webhosts.txt 2.69 kB
Removing Norton Anti-virus 2004, How to remove the Registry Enteries.txt 0.97 kB
Rename ‘recycle Bin’ To Whatever You Want.txt 0.66 kB
Reregister All .dll Files Within Registry.txt 1.54 kB
Reset your lost Bios Password.txt 4.24 kB
Restore JPG,JPEG,JPE Default File associations, Win XP Tweak.txt 1.28 kB
REVERSE CODING.txt 15.11 kB
Run Aol Without Using Aol Browser & Save Resources, connect permanently and use any browser.txt 0.44 kB
Running A Board forum From Your Own Pc.txt 2.32 kB
Running Vanishing Console Programs With A Click!, Ever had a console program that vanis….txt 1.13 kB
Safely Editing the Registry….txt 1.86 kB
Save Your Desktop Icon Settings.txt 2.18 kB
Saving and loading Photoshop actions.txt 1.79 kB
Scheduled Tasks – Defrag, how to set up scheduled defrags.txt 1.92 kB
ScreenLock Professional v2.0.41.txt 0.04 kB
SEARCH eBOOK in FTP SEARCH ENGINE.txt 0.43 kB
Search For Ebook Server With Google.com.txt 0.35 kB
Search like a real warez d00dz, for warez of course!.txt 0.57 kB
Searching For Something To Download, This may help.txt 0.34 kB
Secret Backdoor To Many Websites.txt 2.09 kB
Secrets Of Lock Picking.txt 53.74 kB
Securing WinXP Pro (with what win-xp has to offer.txt 9.60 kB
Securing your WINDOWS XP computer.txt 1.19 kB
Set Google as your Default Search in IE.txt 0.55 kB
Set Win Explorer to open the folder you want!, Little trick.txt 0.23 kB
sick of inserting winxp cd every time your pc asks, Change Default Location of i386 Folder.txt 3.21 kB
sidebar fix.txt 0.57 kB
Simple Tweaks For Peak Pc Graphics Performance.txt 10.16 kB
Single Click Shutdown.txt 2.82 kB
Single-click To Open An Item…, IF the Folder Options is grayed out.txt 1.19 kB
Slow Loggon Time, one fix for problem.txt 0.96 kB
Slow Opening Of File Dialogs.txt 1.10 kB
Some Cool Site For Tutorials.txt 0.41 kB
Some Google Tricks, again.txt 1.74 kB
Some More Tips To Improve Your Winxp.txt 24.09 kB
Sp2 For Xp Slipstream, Integrate SP2 into your XP CD.txt 10.71 kB
Sp2 Tweaks.txt 3.44 kB
Speed Up Internet.txt 4.46 kB
Speed up menu display.txt 0.54 kB
Speed up Mozilla FireFox.txt 0.45 kB
Speed Up Your Bandwidth By 20% !, Windows uses 20% of your bandwidth.txt 1.02 kB
Speeding up menus in XP.txt 0.27 kB
Speeding up your internet connection under Linux and Windows.html 11.75 kB
Spoofing emails, via telenet.txt 0.41 kB
Standard ASCII Character Set.txt 1.79 kB
Steps to Clean Install XP.txt 8.23 kB
Stop A Restart Process In 3steps.txt 0.29 kB
Stop Annoying Pop-ups Without Pop-up Blockersoutli.txt 1.23 kB
System Changes To Foil Hackers And Browser Hijacke.txt 7.65 kB
System File Checker For Windows Xp.txt 2.26 kB
Tcpip A Mammoth Description, Short and easy-Everything U want to know.txt 50.96 kB
Testing Wattage Consumption Of Your Computer, Measuring your computer’s wattage.txt 9.33 kB
The Antivirus Defense-in-Depth Guide.txt 2.77 kB
The difference between DVD-R, DVD+R, DVD+RW and DVD-RW.txt 3.69 kB
The Modern Phreakers Guide To Beige Boxing.txt 4.32 kB
The Modern Phreakers Guide To Payphones.txt 6.98 kB
The Port Guide, Port number and info.txt 24.64 kB
The Ultimate Guide To Installing Windows Xp Sp2.txt 3.14 kB
Three Ways Of Bypass Starforce Cd Protection.txt 2.48 kB
Tip for shutdown windows – virus.txt 0.39 kB
Tips And Tricks, Windows XP.txt 41.24 kB
Tired Of Reinstalling Windows.txt 2.31 kB
To Get And Show The Ip Via Javascript.txt 0.62 kB
Top 5 Myths About Safe Surfing, PC Magazine.txt 3.36 kB
Transferring Data.txt 6.45 kB
Translating Binary To Text.txt 6.22 kB
Translating Binary to Text2.txt 5.72 kB
Trojan Ports.txt 13.83 kB
Turn MSN Messenger Display Pix into User Pix on XP.txt 2.50 kB
Turn Off Unneeded Services, speed up pc.txt 1.56 kB
Tutorial Get the serial number you need.txt 0.88 kB
Tutorial How to create a bootable Windows XP SP1 CD (Nero).txt 2.17 kB
Tutorials Base Number Systems.html 7.78 kB
Tutorials BASIC C Socket Programming In Unix For Newbies.txt 21.50 kB
Tutorials Basics of am 3mp33j3w.txt 18.64 kB
Tutorials Batch File Programming.txt 41.70 kB
Tutorials BOOLEAN LOGIC GATES.html 14.04 kB
Tutorials C++ Tutorial By Clayman.html 23.77 kB
Tutorials Creating A Simple Hit Counter In PHP.html 8.77 kB
Tutorials Creating A Simple Search Engine In PHP.html 9.62 kB
Where Is Winipcfg In Winxp.txt 0.62 kB
Who’s Seeding The Net With Spyware.txt 5.33 kB
Why wait 35 Seconds at eZshare.txt 1.55 kB
Win 2000 Dr. Watsson.txt 0.23 kB
Windows 2000 Tips & Tricks.txt 4.58 kB
Windows 2003 System Restore, How to activate system restore in W2K3.txt 5.47 kB
Windows Scan Count Down Time.txt 0.54 kB
Windows Shortcuts.txt 12.84 kB
WINDOWS TRUE HIDDEN FILES.txt 9.46 kB
Windows Tweak, Hack Your Start Button.txt 3.25 kB
Windows Xp – Speed Up Your Network and Internet Access.txt 2.70 kB
WINDOWS XP HIDDEN APPS.txt 2.59 kB
Windows XP Registry Tweaks.txt 34.05 kB
Windows XP Startup and Performance Tweaks.txt 1.76 kB
Windows Xp Tips ‘n’ Tricks.txt 28.51 kB
Windows Xp Tweaks, A work in progress.txt 2.98 kB
Windows XP Tweaks.txt 2.37 kB
WinRar Tutorial – Compression profiles, passwords and more.txt 5.78 kB
Winsock 2 Repair.txt 2.10 kB
WinXP 3 Tips.txt 1.87 kB
Winxp Application Defrag, faster access for used programs.txt 0.30 kB
Winxp Applications Startup Time, Decrease your Applications startup time.txt 1.16 kB
WinXP Bootable CD.txt 2.19 kB
Winxp System Response, reboot whitout rebooting.txt 0.61 kB
Winxp Tips And Tricks, Winsock 2 repair.txt 2.19 kB
Xp Auto Install.txt 1.79 kB
Xp Folder View Does Not Stay To You’re Setting., Grab your registry editor and join in.txt 1.87 kB
XP REPAIR INSTALL.txt 5.92 kB
XP Tweaking.txt 15.75 kB
Yahoo + geocities Posts.txt 3.07 kB
Yahoo Messeger, no ad’s.txt 0.83 kB
You Want Lots Of Music, Appz, Anything, Try Dex Hunting.txt 1.47 kB
Your Home Page Nevr Being Changed.txt 0.50 kB
Your Own Home Server – Introduction.txt 11.25 kB






